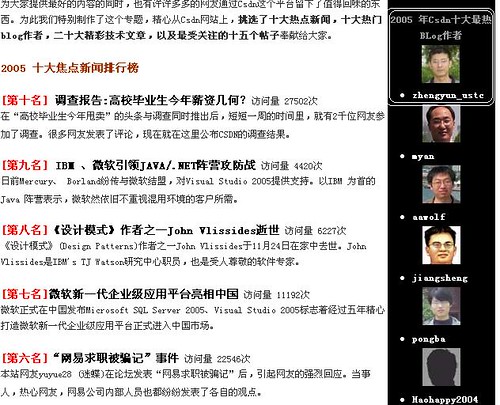
mqtt debian
介绍 (Introduction)
MQTT is a machine-to-machine messaging protocol, designed to provide lightweight publish/subscribe communication to “Internet of Things” devices. It is commonly used for geo-tracking fleets of vehicles, home automation, environmental sensor networks, and utility-scale data collection.
MQTT是一种机器对机器的消息传递协议,旨在为“物联网”设备提供轻量级的发布/订阅通信。 它通常用于车辆的地理跟踪,家庭自动化,环境传感器网络和公用事业规模的数据收集。
Mosquitto is a popular MQTT server (or broker, in MQTT parlance) that has great community support and is easy to install and configure.
Mosquitto是流行的MQTT服务器(或MQTT的代理 ),具有强大的社区支持,并且易于安装和配置。
In this tutorial, we’ll install Mosquitto and set up our broker to use SSL to secure our password-protected MQTT communications.
在本教程中,我们将安装Mosquitto并将代理设置为使用SSL来保护受密码保护的MQTT通信。
先决条件 (Prerequisites)
Before starting this tutorial, you will need:
在开始本教程之前,您需要:
A Debian 10 server with a non-root, sudo-enabled user and basic firewall set up, as detailed in this Debian 10 server setup tutorial.
具有非root用户,启用sudo的用户和基本防火墙设置的Debian 10服务器 ,如本Debian 10服务器设置教程中所述 。
A domain name pointed at your server, as documented in our DigitalOcean DNS product documentation. This tutorial will use
mqtt.example.comthroughout.指向您服务器的域名,如我们的DigitalOcean DNS产品文档中所述 。 本教程将始终使用
mqtt.example.com。An auto-renewable Let’s Encrypt SSL certificate for use with your domain and Mosquitto, generated using the Certbot tool. You can learn how to set this up in How To Use Certbot Standalone Mode to Retrieve Let’s Encrypt SSL Certificates on Debian 10 . You can add
systemctl restart mosquittoas arenew_hookin Step 4. Be sure to use the same domain configured in the previous prerequisite step.使用Certbot工具生成的可自动更新的“让我们加密SSL证书以用于您的域和Mosquitto”。 您可以在如何使用Certbot独立模式来检索让我们在Debian 10上加密SSL证书中学习如何进行设置。 您可以在步骤4中将
systemctl restart mosquitto添加为renew_hook。请确保使用上一个先决条件步骤中配置的相同域。
第1步-安装Mosquitto (Step 1 — Installing Mosquitto)
Debian 10 has a fairly recent version of Mosquitto in its default software repository, so we can install it from there.
Debian 10在其默认软件存储库中有一个相当新的Mosquitto版本,因此我们可以从那里安装它。
First, log in using your non-root user and update the package lists using apt update:
首先,使用您的非root用户登录并使用apt update软件包列表:
- sudo apt update sudo apt更新
Now, install Mosquitto using apt install:
现在,使用apt install安装Mosquitto:
- sudo apt install mosquitto mosquitto-clients sudo apt安装mosquitto mosquitto-clients
By default, Debian will start the Mosquitto service after install. Let’s test the default configuration. We’ll use one of the Mosquitto clients we just installed to subscribe to a topic on our broker.
默认情况下,Debian将在安装后启动Mosquitto服务。 让我们测试默认配置。 我们将使用刚刚安装的Mosquitto客户端之一来订阅经纪人上的主题。
Topics are labels that you publish messages to and subscribe to. They are arranged as a hierarchy, so you could have sensors/outside/temp and sensors/outside/humidity, for example. How you arrange topics is up to you and your needs. Throughout this tutorial we will use a simple test topic to test our configuration changes.
主题是您将消息发布到并订阅的标签。 它们按层次结构排列,因此例如可以具有sensors/outside/temp和sensors/outside/humidity 。 您如何安排主题取决于您和您的需求。 在本教程中,我们将使用一个简单的测试主题来测试我们的配置更改。
Log in to your server a second time, so you have two terminals side-by-side. In the new terminal, use mosquitto_sub to subscribe to the test topic:
第二次登录到服务器,因此并排有两个终端。 在新终端中,使用mosquitto_sub订阅测试主题:
- mosquitto_sub -h localhost -t test mosquitto_sub -h localhost -t测试
-h is used to specify the hostname of the MQTT server, and -t is the topic name. You’ll see no output after hitting ENTER because mosquitto_sub is waiting for messages to arrive. Switch back to your other terminal and publish a message:
-h用于指定MQTT服务器的主机名,而-t是主题名称。 mosquitto_sub ENTER后,您将看不到任何输出,因为mosquitto_sub正在等待消息到达。 切换回另一个终端并发布一条消息:
- mosquitto_pub -h localhost -t test -m "hello world" mosquitto_pub -h localhost -t test -m“ hello world”
The options for mosquitto_pub are the same as mosquitto_sub, though this time we use the additional -m option to specify our message. Hit ENTER, and you should see hello world pop up in the other terminal. You’ve sent your first MQTT message!
对于选项mosquitto_pub是一样的mosquitto_sub ,不过这次我们使用额外的-m选项来指定我们的信息。 按ENTER ,您应该会在另一个终端中看到hello world弹出窗口。 您已经发送了第一条MQTT消息!
Enter CTRL+C in the second terminal to exit out of mosquitto_sub, but keep the connection to the server open. We’ll use it again for another test in Step 5.
在第二个终端中输入CTRL+C退出mosquitto_sub ,但保持与服务器的连接打开。 我们将在步骤5中再次将其用于其他测试。
Next, we’ll secure our installation using password-based authentication.
接下来,我们将使用基于密码的身份验证来保护安装。
步骤2 —配置MQTT密码 (Step 2 — Configuring MQTT Passwords)
Let’s configure Mosquitto to use passwords. Mosquitto includes a utility to generate a special password file called mosquitto_passwd. This command will prompt you to enter a password for the specified username, and place the results in /etc/mosquitto/passwd.
让我们将Mosquitto配置为使用密码。 Mosquitto包含一个实用程序,用于生成名为mosquitto_passwd的特殊密码文件。 该命令将提示您输入指定用户名的密码,并将结果放入/etc/mosquitto/passwd 。
sudo mosquitto_passwd -c /etc/mosquitto/passwd sammy
须藤mosquitto_passwd -c / etc / mosquitto / passwd sammy
Now we’ll open up a new configuration file for Mosquitto and tell it to use this password file to require logins for all connections:
现在,我们将为Mosquitto打开一个新的配置文件,并告诉它使用此密码文件要求所有连接都需要登录:
- sudo nano /etc/mosquitto/conf.d/default.conf 须藤nano /etc/mosquitto/conf.d/default.conf
This should open an empty file. Paste in the following:
这应该打开一个空文件。 粘贴以下内容:
allow_anonymous false
password_file /etc/mosquitto/passwdBe sure to leave a trailing newline at the end of the file.
确保在文件末尾保留换行符。
allow_anonymous false will disable all non-authenticated connections, and the password_file line tells Mosquitto where to look for user and password information. Save and exit the file.
allow_anonymous false将禁用所有未经身份验证的连接,并且password_file行告诉Mosquitto在哪里查找用户和密码信息。 保存并退出文件。
Now we need to restart Mosquitto and test our changes.
现在,我们需要重新启动Mosquitto并测试我们的更改。
- sudo systemctl restart mosquitto sudo systemctl重新启动mosquitto
Try to publish a message without a password:
尝试发布没有密码的消息:
- mosquitto_pub -h localhost -t "test" -m "hello world" mosquitto_pub -h localhost -t“ test” -m“ hello world”
The message should be rejected:
该消息应被拒绝:
Output
Connection Refused: not authorised.
Error: The connection was refused.
Before we try again with the password, switch to your second terminal window again, and subscribe to the ‘test’ topic, using the username and password this time:
在再次尝试使用密码之前,请再次切换到第二个终端窗口,并使用用户名和密码来订阅“ test”主题:
mosquitto_sub -h localhost -t test -u "sammy" -P "password"
mosquitto_sub -h localhost -t test -u“ sammy ” -P“ password ”
It should connect and sit, waiting for messages. You can leave this terminal open and connected for the rest of the tutorial, as we’ll periodically send it test messages.
它应该连接并坐着,等待消息。 在本教程的其余部分中,您可以保持此终端的打开和连接状态,因为我们会定期向其发送测试消息。
Now publish a message with your other terminal, again using the username and password:
现在,再次使用用户名和密码在另一个终端上发布一条消息:
mosquitto_pub -h localhost -t "test" -m "hello world" -u "sammy" -P "password"
mosquitto_pub -h localhost -t“ test” -m“ hello world” -u“ sammy ” -P“ password ”
The message should go through as in Step 1. We’ve successfully added password protection to Mosquitto. Unfortunately, we’re sending passwords unencrypted over the internet. We’ll fix that next by adding SSL encryption to Mosquitto.
该消息应按照步骤1中的顺序进行。我们已成功为Mosquitto添加了密码保护。 不幸的是,我们正在通过互联网发送未加密的密码。 接下来,我们将为Mosquitto添加SSL加密来解决此问题。
步骤3 —配置MQTT SSL (Step 3 — Configuring MQTT SSL)
To enable SSL encryption, we need to tell Mosquitto where our Let’s Encrypt certificates are stored. Open up the configuration file we previously started:
要启用SSL加密,我们需要告诉Mosquitto我们的“加密”证书的存储位置。 打开我们之前开始的配置文件:
- sudo nano /etc/mosquitto/conf.d/default.conf 须藤nano /etc/mosquitto/conf.d/default.conf
Paste in the following at the end of the file, leaving the two lines we already added:
在文件末尾粘贴以下内容,保留我们已经添加的两行:
. . .
listener 1883 localhost
listener 8883
certfile /etc/letsencrypt/live/mqtt.example.com/cert.pem
cafile /etc/letsencrypt/live/mqtt.example.com/chain.pem
keyfile /etc/letsencrypt/live/mqtt.example.com/privkey.pemAgain, be sure to leave a trailing newline at the end of the file.
同样,请确保在文件末尾保留换行符。
We’re adding two separate listener blocks to the config. The first, listener 1883 localhost, updates the default MQTT listener on port 1883, which is what we’ve been connecting to so far. 1883 is the standard unencrypted MQTT port. The localhost portion of the line instructs Mosquitto to only bind this port to the localhost interface, so it’s not accessible externally. External requests would have been blocked by our firewall anyway, but it’s good to be explicit.
我们将两个单独的listener块添加到配置中。 第一个listener 1883 localhost更新端口1883上的默认MQTT侦听器,这是我们到目前为止一直在连接的端口。 标准的未加密MQTT端口1883 。 该行的localhost部分指示Mosquitto仅将此端口绑定到localhost接口,因此无法从外部访问它。 无论如何,外部请求都将被我们的防火墙阻止,但最好是明确的。
listener 8883 sets up an encrypted listener on port 8883. This is the standard port for MQTT + SSL, often referred to as MQTTS. The next three lines, certfile, cafile, and keyfile, all point Mosquitto to the appropriate Let’s Encrypt files to set up the encrypted connections.
listener 8883在端口8883上设置了加密的侦听器。 这是MQTT + SSL的标准端口,通常称为MQTTS。 接下来的三行certfile , cafile和keyfile均将Mosquitto指向相应的“让我们加密”文件以建立加密连接。
Save and exit the file, then restart Mosquitto to update the settings:
保存并退出文件,然后重新启动Mosquitto以更新设置:
- sudo systemctl restart mosquitto sudo systemctl重新启动mosquitto
Update the firewall to allow connections to port 8883.
更新防火墙以允许连接到端口8883 。
- sudo ufw allow 8883 须藤ufw允许8883
Output
Rule added
Rule added (v6)
Now we test again using mosquitto_pub, with a few different options for SSL:
现在,我们再次使用mosquitto_pub测试,并为SSL提供一些不同的选项:
mosquitto_pub -h mqtt.example.com -t test -m "hello again" -p 8883 --capath /etc/ssl/certs/ -u "sammy" -P "password"
mosquitto_pub -h mqtt.example.com -t test -m“再次打招呼” -p 8883 --capath / etc / ssl / certs / -u“ sammy ” -P“ password ”
Note that we’re using the full hostname instead of localhost. Because our SSL certificate is issued for mqtt.example.com, if we attempt a secure connection to localhost we’ll get an error saying the hostname does not match the certificate hostname (even though they both point to the same Mosquitto server).
请注意,我们使用的是完整的主机名,而不是localhost 。 由于我们的SSL证书是为mqtt.example.com颁发的, mqtt.example.com ,如果尝试与localhost进行安全连接,则会收到一条错误消息,指出主机名与证书主机名不匹配(即使它们都指向同一台Mosquitto服务器)。
--capath /etc/ssl/certs/ enables SSL for mosquitto_pub, and tells it where to look for root certificates. These are typically installed by your operating system, so the path is different for Mac OS, Windows, etc. mosquitto_pub uses the root certificate to verify that the Mosquitto server’s certificate was properly signed by the Let’s Encrypt certificate authority. It’s important to note that mosquitto_pub and mosquitto_sub will not attempt an SSL connection without this option (or the similar --cafile option), even if you’re connecting to the standard secure port of 8883.
--capath /etc/ssl/certs/为mosquitto_pub启用SSL,并告诉它在哪里寻找根证书。 这些通常是由您的操作系统安装的,因此Mac OS,Windows等的路径是不同的mosquitto_pub使用根证书来验证Mosquitto服务器的证书已由Let's Encrypt证书颁发机构正确签名。 需要特别注意的是,即使您要连接到标准安全端口8883 ,如果没有该选项(或类似的--cafile选项), mosquitto_pub和mosquitto_sub也不会尝试进行SSL连接。
If all goes well with the test, we’ll see hello again show up in the other mosquitto_sub terminal. This means your server is fully set up! If you’d like to extend the MQTT protocol to work with websockets, you can follow the final step.
如果测试一切顺利,我们将在另一个mosquitto_sub终端中再次看到问候 。 这意味着您的服务器已完全设置好! 如果您想扩展MQTT协议以使用websocket,则可以执行最后一步。
步骤4 —通过Websockets配置MQTT(可选) (Step 4 — Configuring MQTT Over Websockets (Optional))
In order to speak MQTT using JavaScript from within web browsers, the protocol was adapted to work over standard websockets. If you don’t need this functionality, you may skip this step.
为了在Web浏览器中使用JavaScript讲MQTT,该协议经过修改可在标准Websocket上工作。 如果不需要此功能,则可以跳过此步骤。
We need to add one more listener block to our Mosquitto config:
我们需要在Mosquitto配置中再添加一个listener块:
- sudo nano /etc/mosquitto/conf.d/default.conf 须藤nano /etc/mosquitto/conf.d/default.conf
At the end of the file, add the following:
在文件末尾,添加以下内容:
. . .
listener 8083
protocol websockets
certfile /etc/letsencrypt/live/mqtt.example.com/cert.pem
cafile /etc/letsencrypt/live/mqtt.example.com/chain.pem
keyfile /etc/letsencrypt/live/mqtt.example.com/privkey.pemAgain, be sure to leave a trailing newline at the end of the file.
同样,请确保在文件末尾保留换行符。
This is mostly the same as the previous block, except for the port number and the protocol websockets line. There is no official standardized port for MQTT over websockets, but 8083 is the most common.
除了端口号和protocol websockets行外,这与上一个块几乎相同。 没有通过Websockets进行MQTT的官方标准化端口,但是8083是最常见的端口。
Save and exit the file, then restart Mosquitto.
保存并退出文件,然后重新启动Mosquitto。
- sudo systemctl restart mosquitto sudo systemctl重新启动mosquitto
Now, open up port 8083 in the firewall.
现在,在防火墙中打开端口8083 。
- sudo ufw allow 8083 sudo ufw允许8083
To test this functionality, we’ll use a public, browser-based MQTT client. There are a few out there, but the Eclipse Paho JavaScript Client is simple and straightforward to use. Open the Paho client in your browser. You’ll see the following:
为了测试此功能,我们将使用基于浏览器的公共MQTT客户端。 那里有一些,但是Eclipse Paho JavaScript Client使用起来简单明了。 在浏览器中打开Paho客户端 。 您会看到以下内容:
Fill out the connection information as follows:
如下填写连接信息:
Host should be the domain for your Mosquitto server,
mqtt.example.com.主机应该是您的Mosquitto服务器
mqtt.example.com的域。Port should be
8083.端口应为
8083。ClientId can be left to the default value, js-utility-DI1m6.
可以将ClientId保留为默认值js-utility-DI1m6 。
Path can be left to the default value, /mqtt.
路径可以保留为默认值/ mqtt 。
Username should be your Mosquitto username; here, we used sammy.
用户名应该是您的Mosquitto用户名; 在这里,我们使用了萨米 。
Password should be the password you chose.
密码应该是您选择的密码。
The remaining fields can be left to their default values.
其余字段可以保留为其默认值。
After pressing Connect, the Paho browser-based client will connect to your Mosquitto server.
按下Connect之后 ,基于Paho浏览器的客户端将连接到您的Mosquitto服务器。
To publish a message, navigate to the Publish Message pane, fill out Topic as test, and enter any message in the Message section. Next, press Publish. The message will show up in your mosquitto_sub terminal.
要发布消息,请导航到“ 发布消息”窗格,填写主题为test ,然后在“ 消息”部分中输入任何消息。 接下来,按发布 。 该消息将显示在您的mosquitto_sub终端中。
结论 (Conclusion)
We’ve now set up a secure, password-protected and SSL-secured MQTT server. This can serve as a robust and secure messaging platform for whatever projects you dream up. Some popular software and hardware that work well with the MQTT protocol include:
现在,我们已经建立了安全的,受密码保护和SSL保护的MQTT服务器。 对于您梦dream以求的任何项目,它都可以充当健壮且安全的消息传递平台。 与MQTT协议配合使用的一些流行软件和硬件包括:
OwnTracks, an open-source geo-tracking app you can install on your phone. OwnTracks will periodically report position information to your MQTT server, which you could then store and display on a map, or create alerts and activate IoT hardware based on your location.
OwnTracks ,您可以在手机上安装的开源地理跟踪应用程序。 OwnTracks将定期向您的MQTT服务器报告位置信息,然后您可以将其存储在地图上并显示在地图上,或者根据您的位置创建警报并激活IoT硬件。
Node-RED is a browser-based graphical interface for 'wiring’ together the Internet of Things. You drag the output of one node to the input of another, and can route information through filters, between various protocols, into databases, and so on. MQTT is very well supported by Node-RED.
Node-RED是基于浏览器的图形界面,用于“连接”物联网。 您可以将一个节点的输出拖到另一个节点的输入,并且可以通过各种协议之间的过滤器将信息路由到数据库等。 NodeTT很好地支持MQTT。
The ESP32 is an inexpensive wifi microcontroller with MQTT capabilities. You could wire one up to publish temperature data to a topic, or perhaps subscribe to a barometric pressure topic and sound a buzzer when a storm is coming!
ESP32是一款具有MQTT功能的廉价wifi微控制器。 您可以将其连接起来以将温度数据发布到某个主题,或者订阅气压主题并在暴风雨来临时发出蜂鸣声!
These are just a few popular examples from the MQTT ecosystem. There is much more hardware and software out there that speaks the protocol. If you already have a favorite hardware platform, or software language, it probably has MQTT capabilities. Have fun getting your “things” talking to each other!
这些只是MQTT生态系统中的一些流行示例。 有更多的硬件和软件可以使用该协议。 如果您已经拥有喜欢的硬件平台或软件语言,则它可能具有MQTT功能。 让您的“事物”互相交谈,祝您玩得开心!
翻译自: https://www.digitalocean.com/community/tutorials/how-to-install-and-secure-the-mosquitto-mqtt-messaging-broker-on-debian-10
mqtt debian
![J2me流媒体技术实现讨论[2]](/images/no-images.jpg)
![J2me流媒体技术实现讨论[1]](http://www.cnblogs.com/Images/OutliningIndicators/None.gif)